The security of online business
Users often perceive internet security as a concept that financial organizations, various companies, and governments should control.
But it is more complicated than it seems. The Internet takes one of the first places in everyday routine, from information search to financial transactions. Therefore, data security should be in the first place and should be ensured by all participants in the global network.
It is no secret that such organizations that process payments should provide the maximum level of user protection to prevent data leakage and a comfortable pastime. No matter what business model the site uses, certain tips can reduce the potential risks of hacker attacks.
The most common types of fraud
Statista says that there are more than 1.7 billion websites in the world and this number is growing constantly.
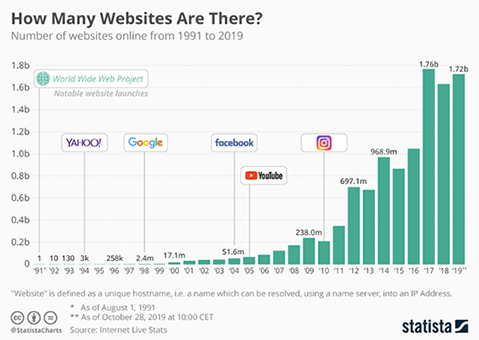
No surprise that such an environment also can be under online fraudsters.
According to statistics released by the Federal Trade Commission, the number of consumer complaints relating to fraud is increasingly growing.
That is why it is so much important to understand how to protect yourself from cybercriminals.
Let’s try to figure out the most common types of online payment fraud:
The paid item was not delivered
The user purchases goods in the online store, but the product does not arrive. Another method that scammers use is when a person buys a ticket online, but upon boarding, he/she finds out that the seat is occupied. Basically, this type of online fraud is traded by fly-by-night sites. To avoid such situations, it is worth buying only from trusted merchants.
Banned account
The user receives a message by an email or phone call, where allegedly a bank employee reports that their bank account or card is blocked. To restore it, they need to provide the card number and CVV code. A fairly common situation when a person under stress actually provides the required data to the scammer. After that, personal funds are stolen. Another type of this type of fraud is when you receive an email with a link to a phishing site.
Phishing
Phishing is a type of Internet fraud, the purpose of which is to obtain user identification data: logins and passwords for bank cards, accounts.
Frequently, phishing is a mass mailing of letters and notifications on behalf of well-known brands, banks, payment systems, postal services, and social networks. Such letters contain a logo, a message, and a direct link to a site that is outwardly indistinguishable from the real one. The link is required to follow the site of the “service” and, under various pretexts, enter confidential data in the appropriate inputs. As a result, fraudsters gain access to user personal and bank accounts.
Phishing attacks can target both individuals and companies. The purpose of attacks on individuals organized by fraudsters, more often, is to gain access to authentication data of banking services, payment systems, various providers, social networks, or postal services. In addition, the purpose of a phishing attack can be to install malware on the victim’s computer.
Fraudulent “dating”
In various online networks and on dating sites, you can often find a soul mate. However, it also happens that the person on the back is a scammer. Imagine that you have made an appointment, but your partner lives in another city or country and does not have enough money to travel. The victim sends the required amount and after that your interlocutor disappears.
Easy earnings
Quite often on the Internet you can stumble upon an advertisement where a presentable-looking man or woman offers a “proven” method of making money. Most often these are sites of online casinos, forex, binary options, etc. In order to lure customers, scammers can offer test accounts with a fixed amount. In this case, the player is “allowed” to win by encouraging him to use real money.
How to prevent online scams?
All owners of online businesses are required to comply with the Competition and Consumer Act. This law is a provision that guarantees users access to complete and transparent information for making informed decisions and excludes unfair terms of the contract.
This agreement helps business owners better understand their obligations to consumers in the context of problems that may arise.
Besides, companies are advised to have legal departments to solve any cases timely.
Online fraud protection is not only about high-quality software.
Educating consumers about the safe use of websites is vital for business owners, users themselves, and law enforcement. All these participants have one goal – security.
Any failure in the overall system is an open door for scammers.
Among the popular methods for detecting and preventing online payment fraud are the following:
- Tokenization.
Instead of using various expensive technologies in an attempt to hide the transaction data, they can be converted into a format that would be useless to a fraudster. This transformed data is called a token. The token can still be the same 16-digit code, which corresponds to the actual number of symbols of a real bank card. This allows you to process data much faster, improve fraud protection, and reduce the cost of additional regulatory requirements. Tokenization is fully PCI DSS compliant.
- Address Verification System.
The Address Verification System(AVS) verifies the billing address provided by the card user with the billing address of the cardholder registered with the issuing bank. This is done as part of the credit card transaction transaction request.
AVS is one of the most common tools used by merchants to prevent credit card fraud, although not the most reliable. The address provided by a bona fide customer may not always match the address registered with the card issuer.
- Data encryption.
There is so-called “end-to-end encryption”. It is a data transfer method in which only the persons involved in the transaction process have access to it. Thus, the use of end-to-end encryption prevents fraudsters from gaining access to confidential information. However, this technology is quite expensive and is more suitable for large businesses.
- Device ID.
Since today many transactions are carried out through mobile applications, the use of data such as device model, geolocation, payment data can help in identifying fraudulent transactions. In the same way, the system can check the data of desktop PCs, including browser type, IP address, operating system.
- Use a reliable payment service provider.
Payment processors, for example PayOp, have built-in fraud detection and fraud prevention software, based on machine learning. Such companies provide merchants’ payments via a secured channel with numerous techniques.
The final thoughts
It should be understood that online fraud is the same dynamically developing system like any other technology. Fraudsters are constantly looking for opportunities to hack and steal users’ personal data.
Reliable payment systems can undoubtedly affect the whole business by providing a variety of mechanisms for providing secure payments.
